Last week, Techcrunch reported rumors of the release of the Google Chrome OS. They stated that the info came from a reliable source, and indeed that source was reliable. Google had an event at their headquarters, and indeed provided new details and a demo of the Chrome OS. The Chromium Blog has some great videos that provide some additional information about Chrome OS as well.
The Chromium OS source code is available for download (Chromium OS is the open-source version of Google Chrome OS), and you can compile and build it. It took some time, but I did manage to do this on my 64-bit Ubuntu 9.04 (Jaunty Jackalope) machine. I also managed to put together a VirtualBox virtual appliance that is all ready to go. I built a torrent for it, so feel free to download it here:
Download the Chromium OS VirtualBox Appliance Torrent
Please continue to seed, as I’m sure there will be many people out there wanting to try it out.
To use it, just start up VirtualBox, click File and then Import. Navigate to the chromiumos.ovf file and select it. The virtual appliance will be imported into VirtualBox and you should be good to go.
I also included a txt file that more or less has the commands I used to build it. You may be able to run it as a script, although I haven’t confirmed that it will work. I guess you could say I more or less took “script-like notes” as I was building Chromium OS.
If you hit Ctrl+Alt+T when you first log in, you’ll get a shell prompt. You can run “sudo su” (no quotes) to log in as root, and I’ve set the password to “password” (no quotes). If you use this machine for anything serious (although I doubt you would), be sure to change the password.
You should be running VirtualBox 3.0.12, and when you import the virtual appliance everything should be configured properly. If you get an error that says “network not connected and offline login fail” when you try to log in, be sure that the virtual network adapter is set to Intel Pro/1000 MT Desktop (82540EM).
If the network adapter is already properly configured but you are still seeing the error, try logging in with the user “chronos” with the password “password” (no quotes). This should log you in and bring up the chrome browser window. If you don’t see a Google Accounts login screen, try hitting the refresh button. That should bring up the Google Accounts login screen.
It is absolutely astounding how fast it boots. It really is nearly instant-on and takes a mere few seconds to bring up the login screen.
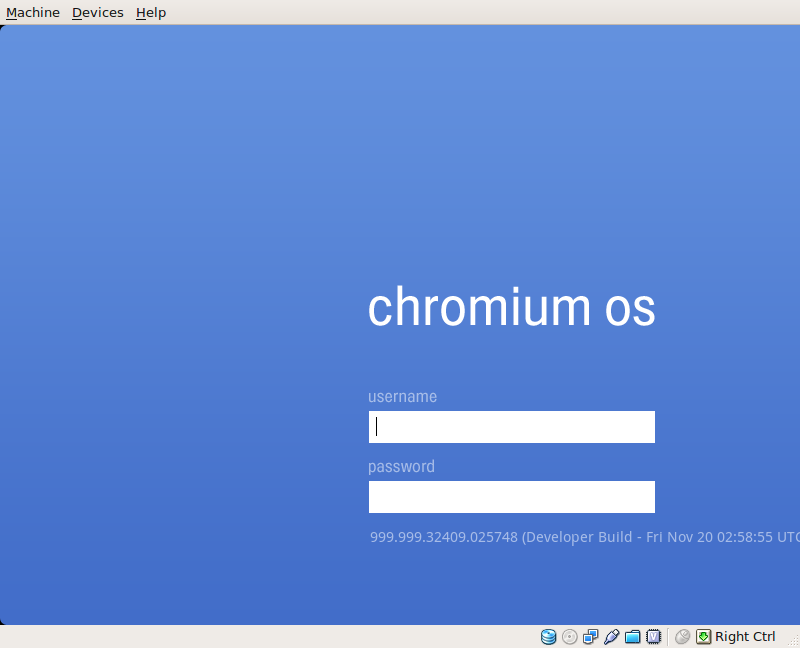
Once you log in with your Gmail account, it launches and you’ll see the Chromium interface open up to your Gmail. There is also a Google Calendar tab and a New Tab tab. The little chrome sphere appears in the upper left corner, but when you click on it you don’t get a menu as you see in some of the Chrome OS videos. Instead, you get a Google.com account login page.
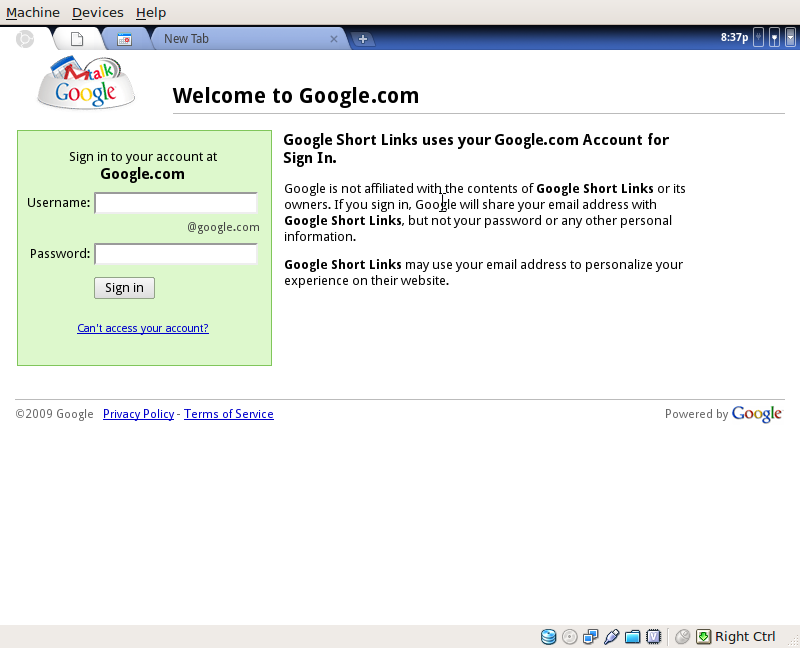
As you can see, it looks very much like the Chrome OS screenshots that had surfaced last month. Of course, being that this is running on a virtual machine without any decent video drivers on the operating system, the resolution is quite low (800×600). Your dear old granddad may be the only one that actually finds it visually appealing at this resolution.
Right now the most impressive thing is how fast this operating system loads. Of course, it should load fast because there really is hardly anything there. In any case, it is rather neat to see an early release in action. The fact that it actually works on a virtual machine is quite promising. Eventually as drivers for more hardware are incorporated into it, it should be possible to run it your own real hardware.
I just went into the Chrome OS Wave I found with the link to the VMWare disk image, and apparently the poor guy that posted that file to Amazon Web Services ran up a $380 bill so he took the file down. Here’s the torrent of the same file posted up on Pirate Bay:
Download the Chromium OS VMWare Virtual Disk Image Torrent
However, I haven’t tried using it, so I can’t confirm that it will run on VMWare without issue. Enjoy your Google Chrome OS virtual machines!
[Via GeekLad]
Mind it, this is a simple copy of the blog entry, I was quite busy in preps of http://clubhack.com/2009 and no time to test this or re-write this :)
No responsibilities if this torrent/VM doesn't work ;)
 1 comments
Thursday, December 31, 2009
1 comments
Thursday, December 31, 2009






 Main Window
Main Window






